Basics of Cybersecurity - Data At Rest
Presentation Overview
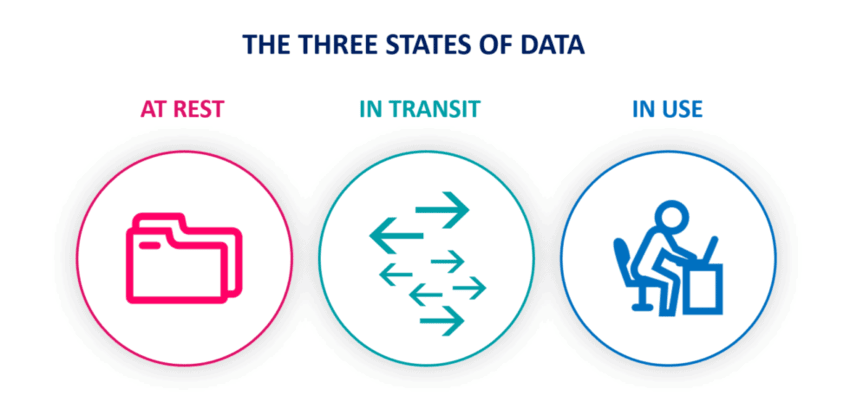
In my presentation to SRMVCAS college students and IT professionals, I covered the critical topic of protecting confidential information by discussing the three states of data: data at rest, data in transit, and data in use. I emphasized the specific protection measures needed for each state and introduced essential data de-identification techniques like pseudonymization, anonymization, and generalization.
Key Takeaways
- Understanding Data States: Recognizing the unique security needs for data at rest, in transit, and in use is crucial for effective protection.
- De-identification Techniques: Employing methods such as encryption and hashing helps organizations comply with regulations like GDPR and HIPAA.
- Practical Applications: Implementing multiple de-identification strategies can significantly reduce the risk of data re-identification.
Impact and Usage
This presentation provided valuable insights into data protection, highlighting best practices that participants can apply in their respective fields. It served to bridge academic knowledge with practical implementation, equipping attendees with the understanding necessary to safeguard sensitive information in an increasingly digital world.